Many process plants contain hazardous materials that, if released, can adversely impact the health and safety of workers and the public, and damage the environment or property. Such releases can result from extraordinary events such as accidents, natural events, or deliberate acts (see figure).
Accidents occur when people make errors or mistakes, or equipment fails. Natural events are phenomena such as lightning strikes and flooding, sometimes called external events. Both are covered by traditional process hazard analysis (PHA) studies.
Deliberate acts, sometimes called malevents, are performed with the intention of causing harm and include terrorism, sabotage, vandalism, and theft. Harm may include the release or diversion of hazardous materials and process or product damage. Some facilities may not contain hazardous materials but may be part of the critical infrastructure for society, for example, pharmaceutical manufacturing. Deliberate acts that damage or disable such facilities also are of concern. Malevents are the security equivalent of an accident.
Most process plants use computer systems to control manufacturing processes and safety systems operation, store information, manage value chain activities, etc. In modern plants, these computer systems often are connected to other networks driven by the need to communicate process information to business groups. This exposes the systems to access by more people and access through the Internet. All these computer systems and their support systems are subject to threats including:
- Manipulation of process equipment such as pumps, valves, and motors to cause a hazardous material release, runaway reaction, diversion of materials, contamination or poisoning of products, etc.
- Misdirecting material transfers.
- Modification of set points for such process parameters as pressure, temperature, and level.
- Disabling or overriding alarms and trip settings.
- Disabling interlocks and safety instrumented systems.
- Disabling visual display units that are required for safe process operation
- Disabling, damaging or destroying cyber assets to prevent their proper operation or cause a financial loss.
- Loss, theft, disclosure, damage, destruction, corruption, or prohibition of access to valuable data or information stored in cyber assets.
- Obtain sensitive information to plan a future attack.
Not all cyber threats are malicious. They can also be caused by accident. People may make mistakes such as incorrectly entering data into computer systems, using the wrong data, accessing the incorrect system, mis-programming systems, using conflicting software, etc.
The objectives of Cyber PHA, sometimes called Cyber Security Vulnerability Analysis (CSVA), are to identify credible cyber threats to a facility, identify vulnerabilities that exist, and provide information to facilitate decisions on any corrective actions that should be taken, such as new or improved security measures and process safeguards.
Cyber PHA is the cyber security equivalent of PHA. It involves evaluating threat events and/or threat scenarios. They originate with hostile action to gain access to processes in order to cause harm. A threat event pairs an attacker and their intent with the object of the attack. A threat scenario is a specific sequence of events with an undesirable consequence resulting from the realization of a threat. It is the security equivalent of a hazard scenario. Threat events are a higher-order representation of detailed threat scenarios. Generally, a threat event represents a set of threat scenarios.
Cyber PHA has several variants. An example is shown in the figure.
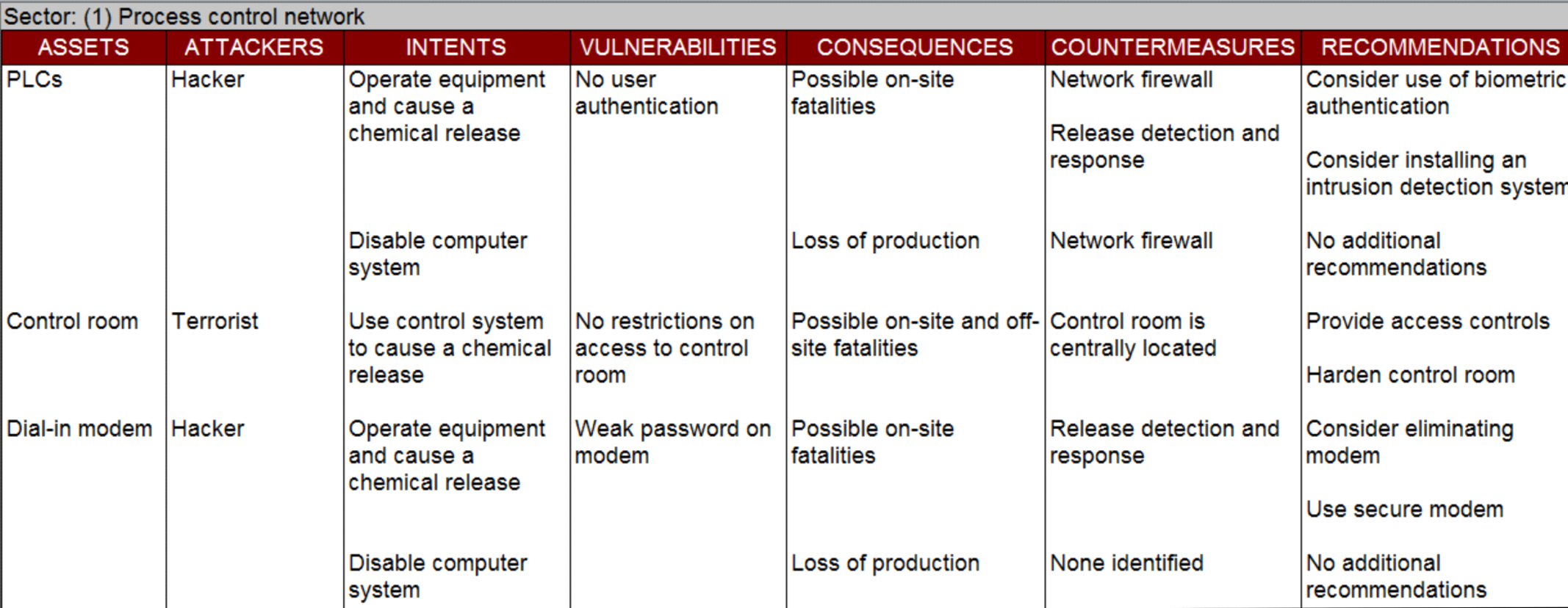
Cyber PHA uses structured brainstorming by a team of qualified and experienced people, a technique that has a long history of success in the safety field. Cyber PHA studies are similar to conventional PHA studies.
Further Reading
Issues for Security Risk Assessment in the Process Industries, Journal of Loss Prevention in the Process Industries, Volume 49, Part B, pages 509-518, September 2017.
Security Vulnerability Analysis: Protecting Process Plants from Physical and Cyber Threats, in Security Risk Assessment in the Chemical and Process Industry, de Gruyter, Berlin, Germany, 2018.
Primatech can assist you with all your process safety needs. Please contact us for further information.

